For the past 25 years InTechnology has been an investment vehicle predominantly owned, controlled and funded by technology entrepreneur, Peter Wilkinson. In a career spanning four decades, Peter has founded a succession of profitable companies and is responsible for the creation of more than 5000 UK jobs.
Over the years, InTechnology has created a number of technology businesses, all of which have been sold. These include Planet Online, Freeserve, Intechnology Specialist Distribution and InTechnology Managed Services.
InTechnology’s ethos has always been to take an idea; build it; prove it; bring it to market; and then sell it to larger businesses which are able to realise the full potential of the technology which has been built.
InTechnology plc’s group of companies are Inhealthcare, WeLink and Mobile Tornado, and it is based in Harrogate North Yorkshire.
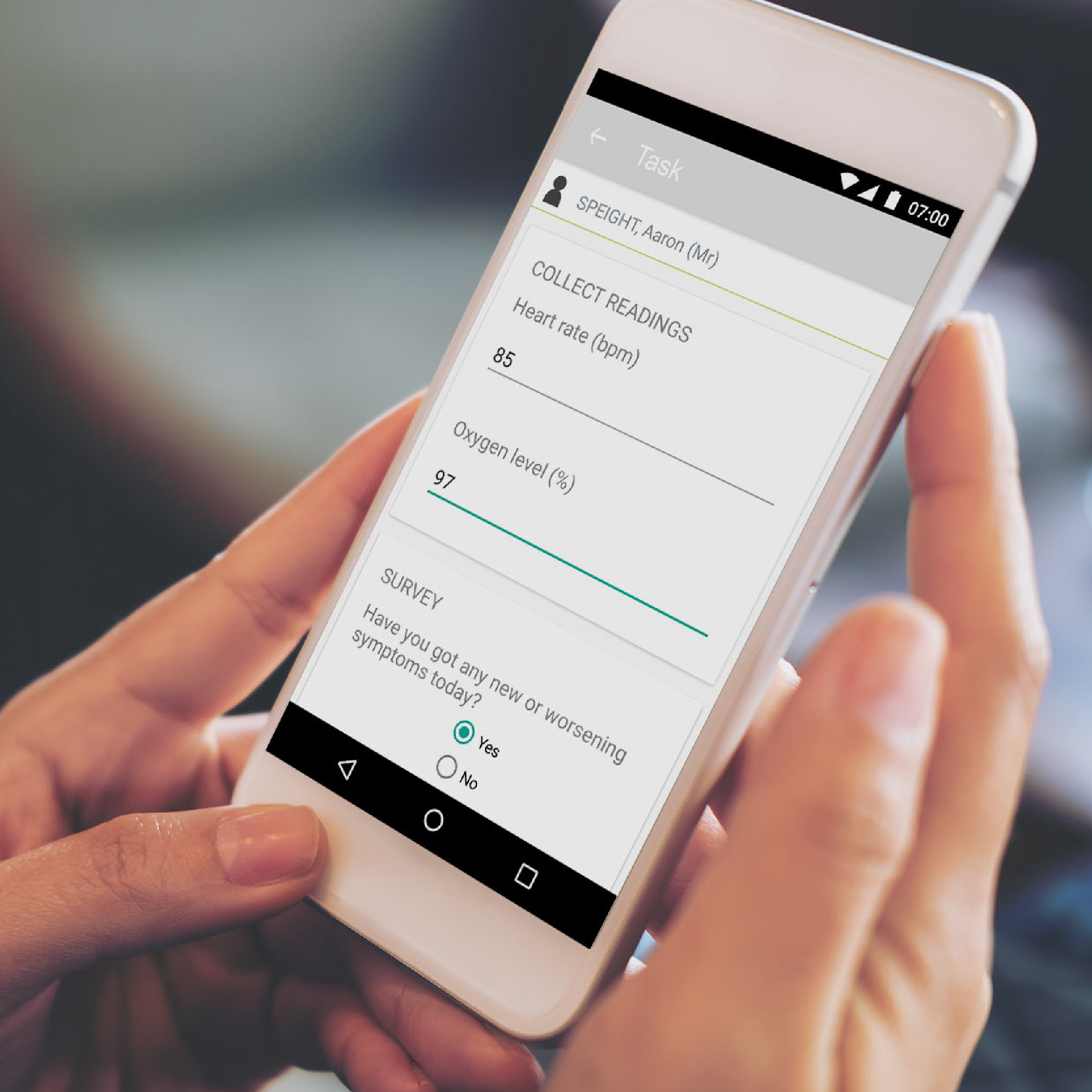
Inhealthcare is the UK’s leading provider of remote patient monitoring services. It has more than 100 clinically designed digital health services and is trusted by more than two million patients. As well as increasing capacity and improving efficiencies in the NHS, Inhealthcare’s remote monitoring services give patients more control over their healthcare and improve outcomes.

Mobile Tornado, a global leader in Push to Talk over Cellular (PoC), with more than 150,000 users and installations across 30 countries in Europe, Africa and the Americas. The Company’s range of solutions comprising of advanced Business Intelligence, AI and workforce management, are geared towards improving the productivity and performance of businesses utilizing state of the art business applications.
![]()
Reliable, efficient broadband makes a real difference to business performance and to people’s everyday lives. WeLink’s unique solution offers superfast, new generation wireless broadband to both businesses and consumers.

Investor Relations
InTechnology plc was incorporated in January 2000 and floated on AIM as an investment company with the intention of acquiring businesses within the then rapidly expanding internet market, primarily in the business to business sector.
In June 2000, Intechnology plc acquired HOLF Technologies Limited and Vdata Limited to form a business that enabled a range of ground breaking cloud computing services to be delivered alongside its specialist computing distribution services.
InTechnology continues to invest where it can utilise its key skills and knowledge to drive innovation in areas in need of joining the digital age.
© Intechnology plc - 35 years of technology innovation